Protect Your Information With Top-Tier Cloud Storage Services
In an age where data safety is extremely important, entrusting your useful information to top-tier cloud storage space services is a strategic action for securing versus prospective dangers. These services surpass plain storage space, providing cutting-edge security methods, stringent access controls, and adherence to sector criteria. By checking out the subtleties of information protection within cloud storage services, you can raise your company's resilience to cyber dangers and ensure the longevity of your digital possessions.
Importance of Data Security

Implementing durable data defense determines aids in maintaining confidentiality, stability, and schedule of information. File encryption converts data into a protected layout that can only be accessed with the proper decryption key, making sure that even if information is intercepted, it continues to be unreadable to unauthorized events.
Advantages of Cloud Storage
In today's electronic landscape, the application of cloud storage space provides many benefits for services and people seeking efficient and secure data management services. One crucial benefit of cloud storage space is its scalability. Users can quickly raise or lower their storage needs without the inconvenience of physical upgrades or hardware installations. This versatility enables expense financial savings and makes sure that storage ability aligns with existing needs.
Users can access their data from any kind of place with a web connection, advertising partnership and remote job capabilities. In addition, cloud storage provides boosted information security procedures such as security, redundancy, and regular back-ups.
Moreover, cloud storage solutions often come with automatic synchronization throughout tools, making certain that the most current version of files is available at all times. Overall, the advantages of cloud storage space make it an important option for modern information administration requires.
Key Attributes to Search For
When evaluating top-tier cloud storage space services, it is important to take into consideration key features that enhance information monitoring effectiveness and safety. A durable cloud storage space solution should provide scalability options to fit your data development without endangering efficiency.
One more vital attribute is data security. Look for a cloud storage solution that provides end-to-end file encryption to protect your information both en route and at remainder. Encryption assists shield your sensitive information from unapproved access, making certain information personal privacy and compliance with laws.
Look for cloud storage solutions that provide my sources partnership functions like real-time editing and enhancing, data versioning, and individual consents control. Prioritizing these essential attributes will certainly help you pick a top-tier cloud storage space service that meets continue reading this your data administration requires efficiently and securely.
Protection Actions and Conformity
Guaranteeing robust protection procedures and compliance criteria is vital for any type of top-tier cloud storage solution company in safeguarding delicate data (linkdaddy cloud services). To attain this, leading cloud storage solutions execute a multi-layered approach to protection. This includes file encryption protocols to secure data both in transportation and at rest, robust accessibility controls to make sure just licensed customers can see or adjust data, and normal security audits to determine and address any type of susceptabilities proactively
Compliance with market laws such as GDPR, HIPAA, or PCI DSS is likewise critical for cloud storage providers. Sticking to these criteria not only assists in shielding data however additionally builds count on with consumers who rely upon these solutions to save their delicate information safely. In addition, top-tier providers commonly undergo third-party safety and security qualifications to show their commitment to preserving high-security requirements.
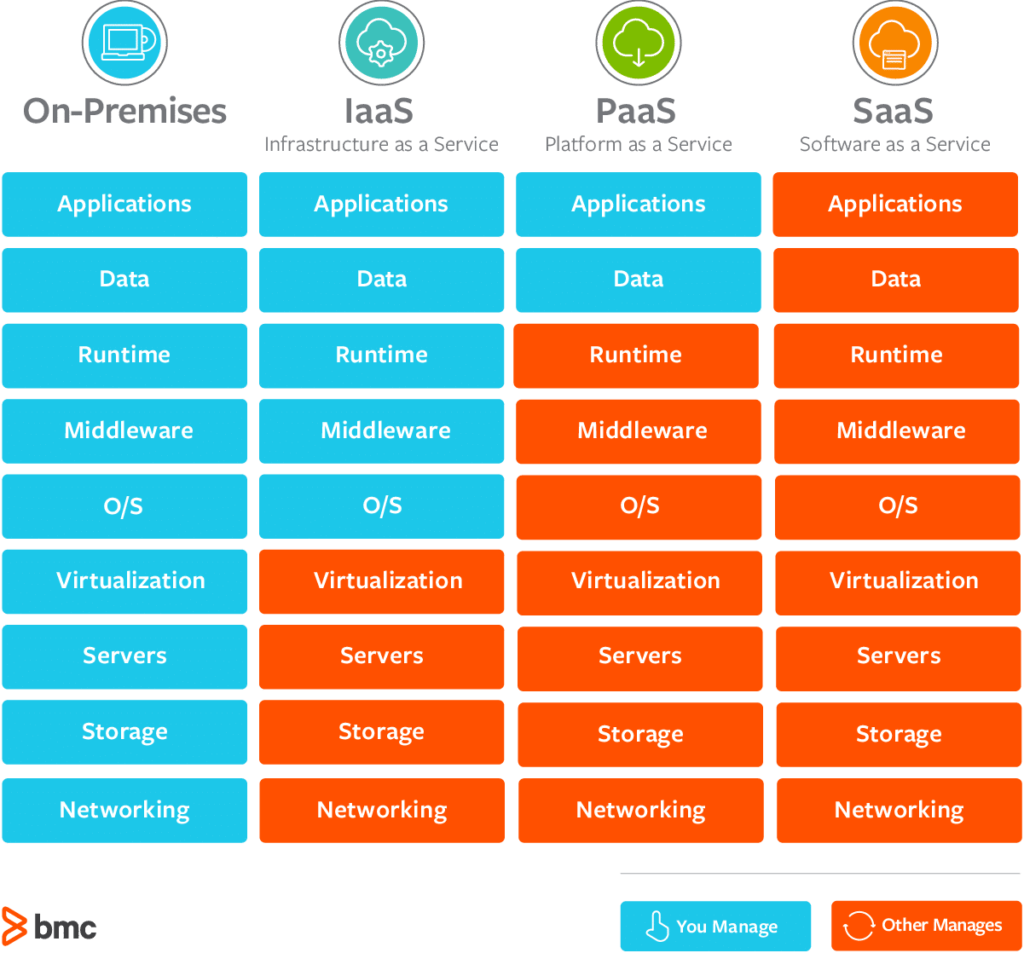
Tips for Picking the Right Service
Make sure that the storage space fulfills your present demands and allows for scalability as your information grows. Next, review the solution's dependability and uptime warranties to lessen possible downtime and guarantee continuous access to your information. Think about the level of safety and security procedures implemented by the company, such as encryption methods and data defense mechanisms, to guard your delicate information.
Final Thought
Finally, securing information with top-tier cloud storage services is crucial in ensuring the safety and honesty of sensitive info. By leveraging durable safety and security steps, encryption procedures, and compliance requirements, organizations can secure their information from cyber hazards and data breaches. Choosing a reputable cloud storage space provider that prioritizes information security is vital for preserving discretion and schedule while taking advantage of scalability and boosted security attributes in the digital age.
With the increasing reliance on electronic data storage space, the danger of cyber dangers and data violations has also expanded.Executing robust information defense measures helps in keeping privacy, integrity, and accessibility of data. web File encryption converts data right into a protected layout that can only be accessed with the appropriate decryption trick, guaranteeing that also if data is obstructed, it continues to be unreadable to unapproved events.Guaranteeing durable security steps and conformity requirements is extremely important for any top-tier cloud storage service supplier in guarding delicate information. By leveraging durable protection measures, encryption protocols, and compliance standards, companies can shield their data from cyber threats and information breaches.